
How we got hacked on GitHub pages
How we got hacked on GitHub pages. And how we fixed it.
You definitely remember those cases when you were hacked! It’s so nasty and shocking! Especially when you see terrorist headline against your nice tech pictures! Shardik was hacked too. And we want to share this story with you.
Intro.
We decided to quit our office jobs to create a company which unites us as independent developers about a year ago. It was an amazing year but this story will be told in another post. Now only about dirty defacing!
We created a website that gives some information about who we are. It’s a good point on the start for any undertaking at the present decade. The website is straightforward and static. That was an experiment, so we were looking for something nice and geeky to host the content. This is how we found Github Pages
To start with we have set up Travis CI Travis builds and deploys the Hugo based website directly to the Pages. Cool!
But, as is often the case, the clients’ work cut off anything else from our day to day routing. And we forgot about the website since it was of no real use.
Time passed, and we decided to return to a branding job.
We bought a new domain - shardik.com
Surprisingly, .software domain zone proved itself as too confused to share with people, especially from non-tech areas.
We have switched the domains in the Pages settings and left everything else in place. As a result, the old domain became unusable.
Mystery begins.
The new domain is bought! Here we go! The next step is looking for a brand new design. Posting a designer job description is unbelievably involved. And this activity was a reason why we opened the old domain by chance.
It was defaced! We found threaten terrorist texts against our nice faces and Shardik stories. It scared us in earnest! (Details are hidden to avoid any advertising.)

Current job was dropped far away.
All related accounts were immediately checked, no suspicious activity found. No session or logins we couldn’t explain. No actions in logs that would reveal the reason. However, still, the website returned unpleasant and aggressive content.
The new domain felt great at the same time. Time to go deeper!

Narrow down the suspects
First of all, we have checked the IP addresses. Both resources have the same IPs returned. How could that be?
We started from the very beginning of the chain. DNS entries for the domains were the same; nothing had changed. So the issue was somehow related to Github.
Next stop was Travis. Maybe attackers could rebuild our website somehow? We’ve checked builds in the list. Nothing outstanding, all builds were triggered by us. Again a blank shot.
So we inspected recent changes done with the configuration. The only meaningful change was a domain switch.
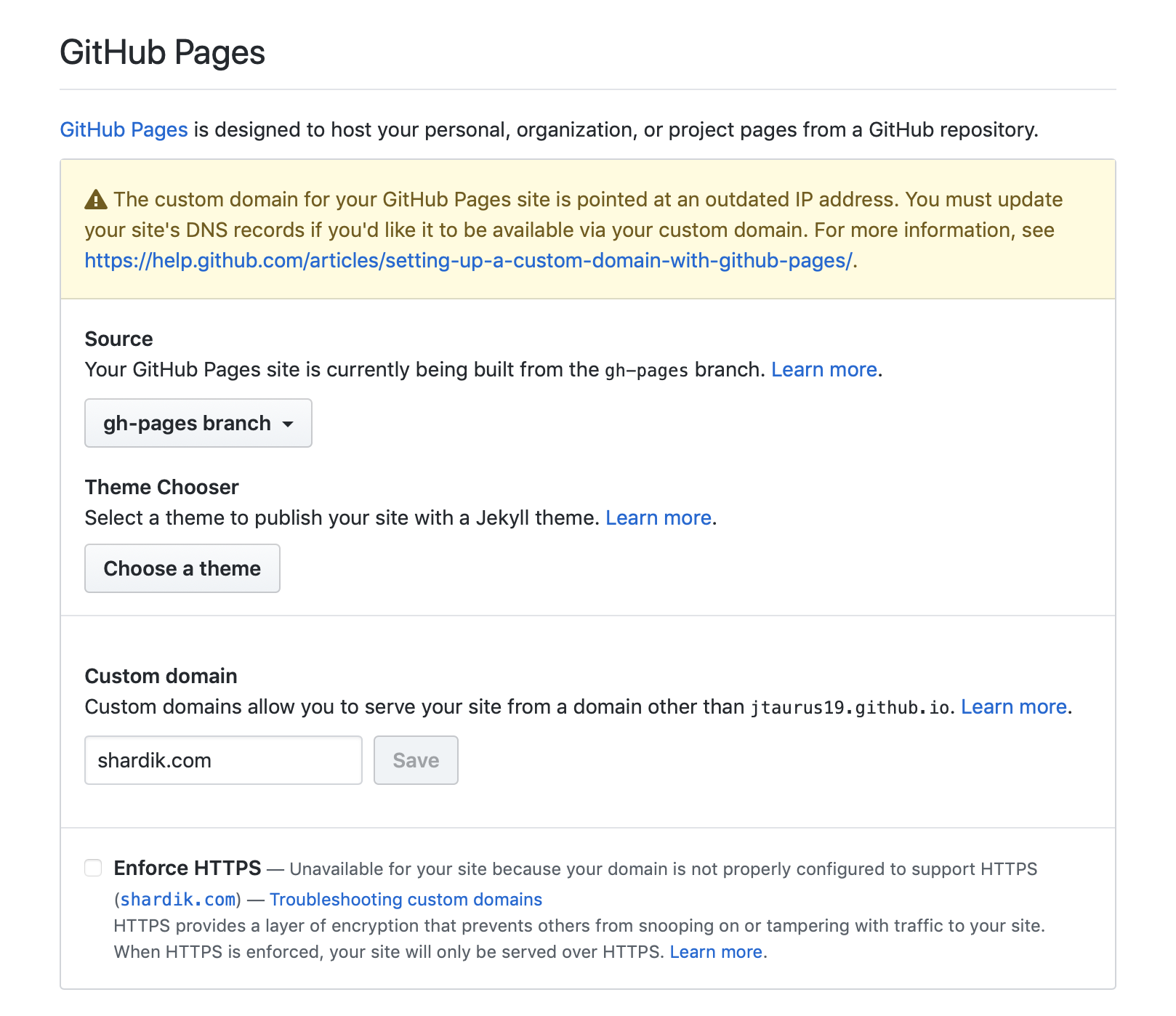
Github Pages allow you to assign only one domain name. What has happened to our old domain in that case? Aha!

Theory and practice
We quickly created a new blank repository to test the assumption. When the repo was there, we tried to assign our old domain to it. Github said that the domain was already in use. That was it! The root cause became clear.
Take actions
We quickly found the evil repository that managed to occupy our domain. There was some automatic script for sure, running already for several days. More than 200 websites were abused at the time of discovery. Github reacted fast, the villain was blocked and the defaced websites became inactive.

Conclusion
It’s not clear why Github doesn’t ask a user to prove the website does belong to him. That is already a widespread procedure that could easily prevent the issue.
Don’t forget to clean up your DNS entries when you stop using the Github Pages.
Stay safe! Shardik with love.
